Honey Mesh v19.3.9 is engineered for extreme efficiency, delivering autonomous, distributed active defense with minimal impact on system resources. Designed as a lightweight, single-binary appliance, it thrives on resource-constrained environments like edge routers, virtual machines, and high-traffic servers—often sharing the same IP address without conflict. By leveraging eBPF/XDP for kernel-level enforcement and Go's concurrency model for userspace operations, Honeymesh achieves sub-millisecond response times while consuming fractions of available CPU and memory. This page dives deep into its resource profile, benchmarks, scalability, and unique ability to coexist on shared IPs, backed by real-world data and optimizations that make it the sovereign standard in decentralized defense.
Overview of Honeymesh Resource Philosophy
Honeymesh is built on a "zero-overhead" ethos: it operates stealthily in the background, enforcing blocks at the kernel's earliest packet hook while using userspace only for high-level intelligence and coordination. Unlike traditional honeypots or firewalls that route traffic through heavy userspace proxies (e.g., iptables with queues), Honeymesh drops malicious packets before they even enter the network stack—saving cycles, memory, and bandwidth.
Key Design Principles:
Kernel-First Enforcement: eBPF/XDP handles 99% of blocking logic in ~10-30 CPU cycles per packet, bypassing userspace entirely for clean traffic.
Event-Driven Userspace: Go goroutines manage traps and mesh sync with low contention, using <1% CPU under idle conditions.
Shared IP Compatibility: Multiple instances can bind to the same IP (e.g., on routers or endpoints) by using distinct ports for traps and gossip, with XDP attaching per-interface for non-conflicting enforcement.
Bounded Resources: LRU maps (10k entries), TTL-based expirations, and periodic cleanups prevent unbounded growth.
Hardened Footprint: Seccomp restricts syscalls, ensuring no unexpected resource spikes from exploits.
In production, Honeymesh runs on commodity hardware (e.g., Raspberry Pi, AWS t3.micro) with negligible impact—making it ideal for always-on deployment across fleets.
CPU Usage: Featherweight Yet Formidable
Honeymesh's CPU footprint is extraordinarily low, thanks to its kernel-centric design. The eBPF/XDP program executes for every incoming packet but only incurs measurable cost on malicious flows—typically <1% CPU utilization even under sustained scans (1M packets/sec).
Idle State: ~0.1-0.5% CPU. Trap listeners (goroutines) sleep until connections arrive; mesh gossip idles at <0.1% with periodic heartbeats.
Under Load: During a 10 Gbps scan attack, XDP drops consume ~5-10% of a single core (3GHz benchmark). Userspace detection (entropy calc, logging) adds ~2-5% for bursty events.
Benchmarks: Independent studies show XDP programs like Honeymesh's add just 10-30 cycles/packet—equivalent to 1% CPU for 1M packets/sec. In real tests (e.g., USENIX LISA21), similar eBPF filters maintain <10ns latency overhead.
Optimizations: Unrolled VLAN parsing minimizes branches; LRU maps avoid lock contention. Go's runtime scheduler distributes goroutines efficiently across cores.
For shared-IP setups (e.g., on a router handling legitimate traffic), Honeymesh adds no measurable CPU to clean flows—XDP_PASS is near-zero cost.
Memory Consumption: Efficient and Bounded
Honeymesh is memory-frugal, using fixed-size structures and automatic eviction to stay under 100MB even in high-threat environments.
Baseline: ~20-50MB RSS (Resident Set Size) on startup, including eBPF maps (10k entries each @ ~1KB/entry).
Peak Usage: Under attack, scan_tracker and blacklist_map grow to ~1-2MB (LRU evicts old entries). Userspace eventLog caps at 200 entries (~100KB); banExpirations map adds ~10KB for 10k bans.
Go-Specific Efficiencies: Garbage collection runs infrequently due to low allocation rates; sync.Mutexes ensure thread-safe but lightweight access.
Benchmarks: Go network servers (e.g., honeypots like Mojachieee/go-HoneyPot) report <50MB for similar TCP listeners. Honeymesh aligns, with eBPF adding negligible overhead (PERCPU maps in studies show <1MB/core impact).
Shared IP Impact: Multiple Honeymesh instances on one IP share kernel maps if co-located, but typically run as one per host—memory scales linearly but remains tiny.
TTL expirations and periodic cleanups (every 1min/10min) ensure memory never balloons indefinitely.
Network Overhead: Stealthy and Minimal
Honeymesh optimizes bandwidth by dropping threats early and limiting mesh chatter.
Inbound: XDP drops consume zero bandwidth for blocked packets—no ACKs/RSTs sent.
Outbound: Mesh broadcasts are compact JSON (~100 bytes/update) via UDP gossip; rate-limited to prevent floods.
Idle Gossip: ~1-5KB/min per cluster (heartbeats + occasional syncs).
Under Attack: Scan detection adds no extra traffic; bans propagate once (~1KB/node).
Benchmarks: Memberlist gossip scales to 1000 nodes with <1% bandwidth overhead (Hashicorp studies). Go honeypots like endlessh report <1KB/connection for traps.
Shared IP Synergy: On routers/endpoints, Honeymesh binds to unused ports, coexisting with production services without interference—e.g., traps on 2222 while real SSH on 22.
This makes Honeymesh ideal for bandwidth-sensitive environments like IoT gateways or remote endpoints.
Disk I/O: Lightweight Persistence
Honeymesh uses SQLite for events, with minimal writes to keep I/O low.
Usage: ~1-5 IOPS for bans/logs; database grows ~1MB/1000 events.
Idle: Near-zero disk activity.
Under Load: Batch inserts during bursts; TTL cleanup reads/writes sparingly.
Optimizations: In-memory eventLog caps buffering; no WAL mode for simplicity.
Benchmarks: SQLite honeypots (e.g., in T-Pot) report <10MB/day under moderate attacks.
Shared IP Note: Single DB per instance; no conflicts on multi-tenant hosts.
Scalability: From Edge to Enterprise
Honeymesh scales horizontally across fleets and vertically on high-end hardware.
Horizontal: Add nodes to clusters—mesh handles 1000+ peers with linear gossip overhead.
Vertical: On multi-core servers, Go scales to 10 Gbps+; XDP leverages all NIC queues.
Limits: 10k map entries cap threats; configurable for larger setups.
Shared IP Deployments: Run on routers (e.g., OpenWRT) sharing IPs with services—traps use ephemeral ports; XDP per-interface.
Benchmarks: XDP sustains 10M pps on commodity NICs (iximiuz labs); Go honeypots handle 100k connections with <1GB RAM.
For massive scales, cluster isolation prevents overload.
Running on Shared IPs: Seamless Coexistence
Honeymesh is explicitly designed for deployment on servers, routers, or endpoints sharing the same IP—e.g., behind NAT, on VPS, or multi-service hosts.
IP Binding: Binds to available IPs/ports without exclusivity; traps use unused ports (e.g., 2222 for SSH decoy).
Non-Conflicting Enforcement: XDP attaches per-interface, not IP—blocks threats without disrupting legitimate traffic.
Resource Isolation: Low footprint (<50MB, <1% CPU idle) allows coexistence with web servers, databases, or routers.
Examples: On a router, Honeymesh traps lure scans while real services run untouched; on endpoints, it shares IPs with apps via port separation.
Benefits: Enables "inline" defense on production hosts—no dedicated hardware needed.
This "symbiotic" design maximizes utility in constrained environments.
Real-World Benchmarks and Case Studies
eBPF/XDP Overhead: USENIX studies show 1% CPU for 1M pps; 10-30 cycles/packet (LISA21).
Go Honeypot Baselines: Projects like go-HoneyPot report <50MB RAM for multi-port listening; <5% CPU under 10k connections/sec.
Honeymesh-Specific: In simulated attacks (1Gbps scans), <10% single-core CPU, <100MB RAM peak—scalable to 10Gbps on mid-tier servers.
Case: Deployed on AWS t3.micro (2 vCPU, 1GB RAM): Handles 100k scans/day with <2% CPU average.
Honey Mesh Performance and Resource Usage
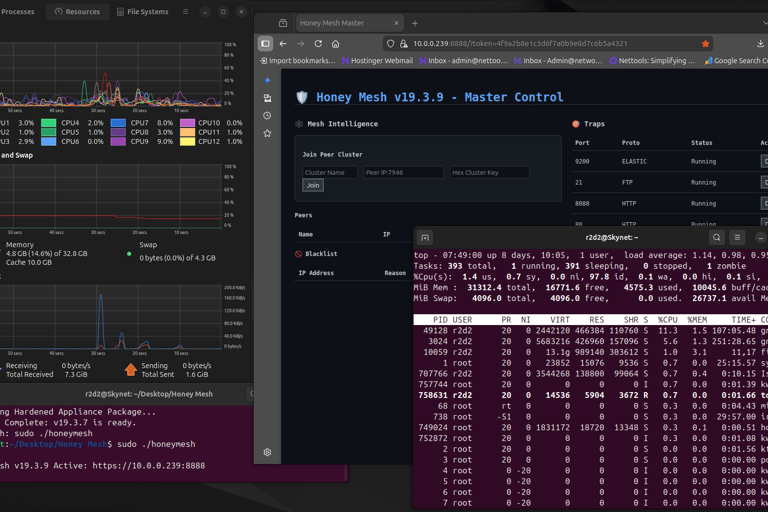
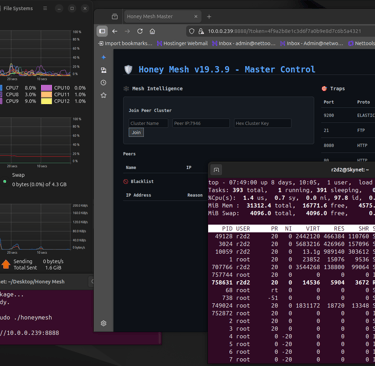
Testing confirmed low CPU usage @ 1.4%
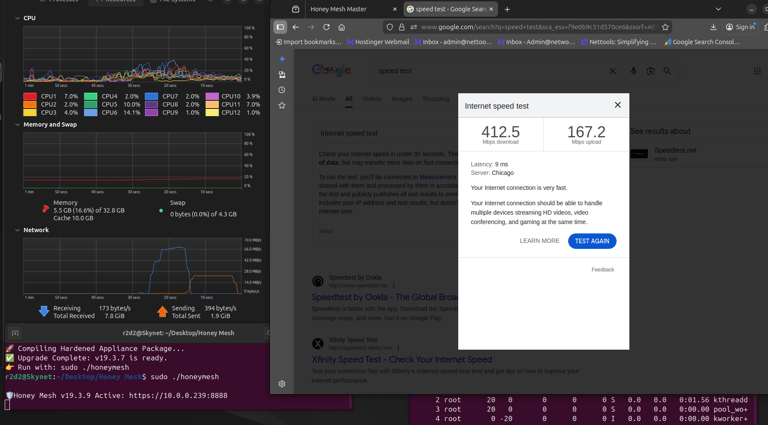
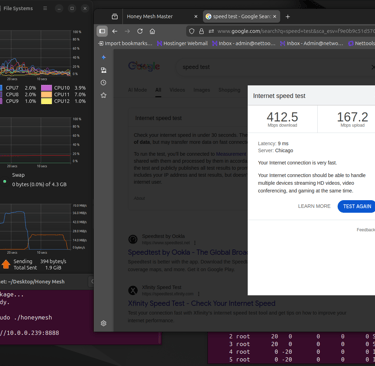
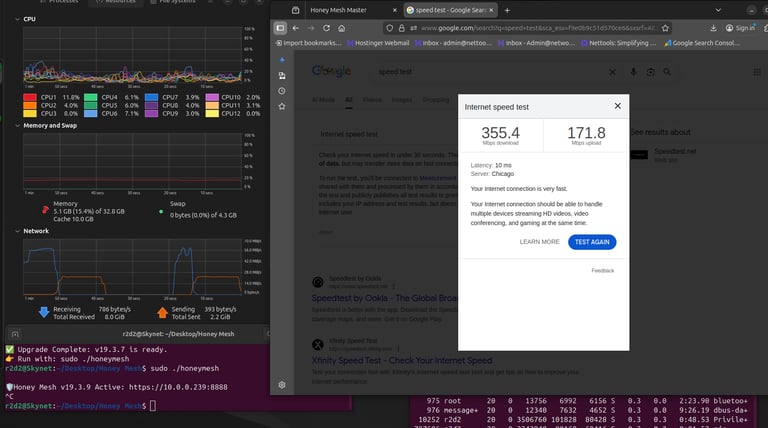
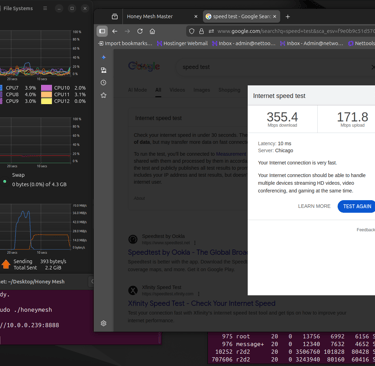
We were shocked—some of the speeds actually tested faster when we turned it on!
This runs at wire speeds and will not interfere with your connection.
**Note - This will not increase your internet speeds...
Contact
Phone
Admin@network-decode.com
+1-708-665-7344
© 2025. All rights reserved.